
Shifting Left in Automotive Cyber Security: An ROI-Driven Approach for Vehicle Vulnerability Management
The explosive growth in vehicle software, driven by the emergence of software-defined vehicles (SDVs), has introduced major security challenges for the automotive industry. The math is simple: the more software you have in a vehicle, the greater the risk of having a vulnerability. To minimize potential safety and privacy risks and to comply with new cyber security regulations and standards, OEMs and Tier 1s are deploying vulnerability management systems.
At the same time, as more and more automakers adopt CI/CD (Continuous Integration/Continuous Delivery) techniques, including OTA updates and frequent software releases for critical components, we’re seeing a shift towards integrating vehicle vulnerability management (VVM) earlier in product development.
Let’s take a look at some of the advantages of this “shift left” approach, as well as examples of VVM integration with commonly used CI/CD tools.
Why Automotive-Specific Vulnerability Management Is Crucial
Automotive-specific VVM solutions are built to meet the unique safety and complexity challenges posed by modern vehicles. Beyond identifying software vulnerabilities, these tools integrate features like asset management, AUTOSAR compatibility, and even the ability to address hardware vulnerabilities in Electronic Control Units (ECUs).
For example, to pinpoint vulnerabilities in vehicle assets, vulnerability management tools need to navigate the intricate hierarchies of automotive ECUs, which often include components from multiple suppliers. Unlike traditional IT tools, automotive-specific solutions fill this gap by offering targeted visibility into these hierarchies, allowing for more effective and precise mitigation strategies.
Another vulnerability management challenge is that automotive ECUs often come without a pre-defined SBOM. Automotive-specific VVM tools are engineered to automatically extract this information from binary files, including from automotive specific AUTOSAR ECUs, thus enabling manufacturers to manage vulnerabilities with a level of granularity that general-purpose tools cannot provide.
Early Detection of Vulnerabilities Leads to Faster Resolution
As noted, many Tier 1 suppliers are already implementing CI/CD techniques to accelerate their coding and testing processes. Some develop the software code for ECUs and other components from scratch, while others work with multiple lower-level software suppliers.
Due to the complexity of the automotive supply chain, Tier 1s are not always aware of the software composition of the ECU components they receive from their downstream suppliers. To scan this code for vulnerabilities prior to shipping to the OEM (which has become a de facto demand), Tier 1s need full visibility into the code during the development process.
Integrating vulnerability management tools with other tools in the CI/CD pipeline allows Tier 1s to automatically detect vulnerabilities at the earliest stages of development. This proactive approach helps address vulnerabilities up front, allowing engineers to resolve issues much faster and cost-effectively.
How to Integrate VVM in Your CI/CD Pipeline
So, what does VVM integration look like from the software developer’s perspective? Let’s consider a sample scenario where VVM is integrated with Jenkins for automated building and testing of software, and with Jira for tracking and management of vulnerability resolution.
This integration allows developers to scan the code for vulnerabilities as part of the testing phase within Jenkins. The benefit here is that you don’t have to manually download/upload files between Jenkins and the VVM, and you can get immediate feedback regarding the build’s security status. For example, you can create rules in Jenkins to decide whether to pass or fail the build based on the number and severity of the vulnerabilities discovered.
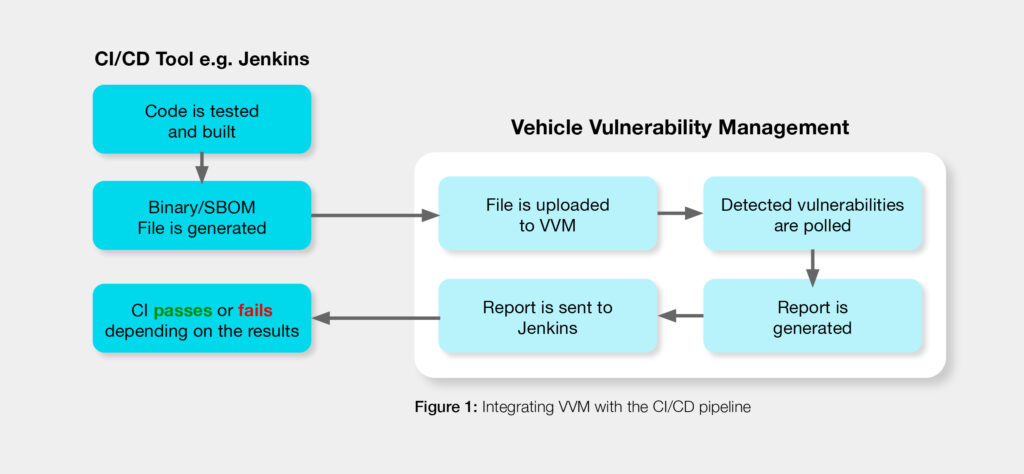
Integrating VVM with Jenkins
Let’s assume for this example that VVM detects a critical vulnerability on a specific ECU. By integrating the VVM tool with a project management tool, such as Jira, the analysis and mitigation tasks are assigned to the relevant person on your internal project or development team. From within Jira, your cyber analysts receive all the information (the “User Story”) they need to analyze the vulnerability, understand how to resolve it, and then deploy the mitigation.
If your company is using different CI/CD tools or even legacy systems for product development and testing, it’s important to check that your VVM solution supports the necessary APIs to seamlessly integrate within your CI/CD pipeline structure. Vendors offer varied levels of API documentation and support options that can help you achieve a smooth integration.
Shifting to Proactive Vehicle Vulnerability Management
In automotive software and hardware design, vulnerabilities are an inherent challenge. Recognizing this, it’s essential for Tier 1s to prioritize identifying and addressing these issues before they become significant risks.
Proactive vulnerability management solutions can help cyber security managers detect and resolve vulnerabilities as an integral part of the CI/CD pipeline. Moving vulnerability detection to an earlier stage of the design process (along with testing and QA) will help Tier 1s save time, effort and costs, while accelerating time to market.
Interested in learning more about the advantages of integrating Vehicle Vulnerability Management in your CI/CD pipeline?






