UNECE WP29 Automotive Cybersecurity Regulation
Status: Published
Published Date: June 2020
Region: Global
Document: Link
UNECE WP29 Automotive Cybersecurity Regulation
Background on the UNECE WP29 Automotive Cybersecurity Regulation
WP.29 is the World Forum for the Harmonization of Vehicle Regulations which defines the process of type approval for and mutual recognition of wheeled vehicles, equipment, and parts. WP.29 is part of the United Nations Economic Commission for Europe (UNECE) and forms the largest international vehicle regulatory system in the world. Its primary responsibility is to keep its vehicle regulations updated and relevant, especially in the context of changes in technology, safety, and environmental protection.
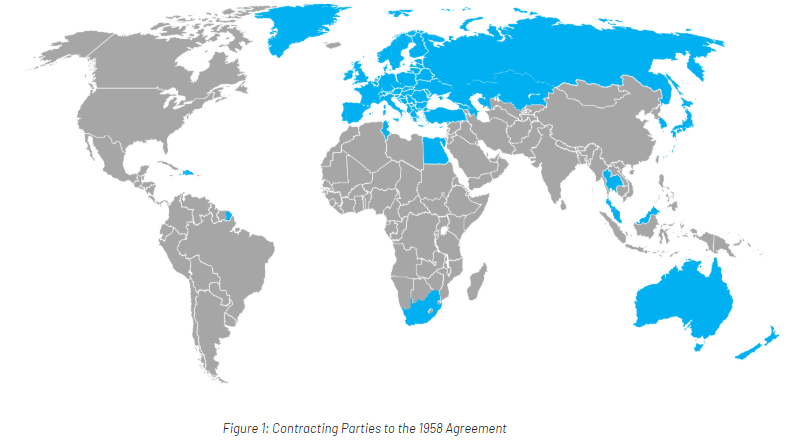
As of 2020, the contracting parties (CPs) to UNECE’s 1958 agreement have grown to 54 including all EU countries and other OECD nations (see Figure 1 below) like Japan, Turkey, Russia, Australia, and South Africa.
The latest WP.29 document relating to cybersecurity becomes the first regulation that mandates cybersecurity in connected and autonomous vehicles.
Summary
WP.29 cybersecurity regulation outlines requirements for new vehicles and the organizations that manufacture them. The cybersecurity requirements described are for the purpose of obtaining approval for new vehicle types with regards to cybersecurity.
The regulation currently applies to vehicles of category M and N (mainly – vehicles with 4 wheels or more with specific load capacities) – with more categories (O, R, S and T) under consideration. The regulation will also apply to more categories if equipped with automated driving functions beyond level 3.
The regulation divides type approval into two very distinct parts – requirements of the manufacturer’s CSMS and requirements for the vehicles themselves.
Requirements of the Cyber Security Management System (CSMS) – Section 7.2 of the regulation:
Organizational structure: Each manufacturer must demonstrate a risk-based management framework for discovering, analyzing and protecting against relevant threats, vulnerabilities, and cyber attacks, their “CSMS.” The processes used by the manufacturer to do this must apply to the development, production and post-production stages (as defined above) of the vehicle lifecycle. And, the manufacturer must obtain for its organization a “certificate of CSMS compliance” before its vehicles are eligible to be considered for type approval with regards to cybersecurity.
Organizational processes: Included in the requirements for CSMS compliance is the necessity to show how the threats and mitigations listed in the regulation’s Annex 5, were “adequately considered,” during vehicle development. Annex 5 provides a comprehensive list of known threats to vehicles as well as relevant mitigations for them. If a threat or mitigation was not included in the manufacturer’s risk assessment or vehicle design, the manufacturer must provide an explanation as to why it was deemed out of scope and what alternative factors and measures were considered and taken in order to identify and reduce risk to the relevant vehicle system(s).
Organizational processes: built for risk identification, categorization, and treatment that continue through the stages of the vehicle’s lifecycle. These processes should prove that risks are and will be “appropriately managed,” that the cybersecurity of the vehicle is, and will be, tested (recursively if necessary) and that the risk assessment for the vehicle is kept up to date at any given time throughout the vehicle’s lifecycle. Additional functions and measures are expected to be in place regarding the vehicle’s components and/or systems that have been deemed “critical elements” (elements at high-risk) within the manufacturer’s risk assessment for the vehicle.
CSMS Functions: Organizational functions must be in place to support monitoring, detecting and responding to cyberattacks, threats, and vulnerabilities during the vehicle’s post-production stage (i.e., while on the road). The processes used by the manufacturer to digest and the information generated by these functions should demonstrate how the cybersecurity measures that are implemented will remain effective once new threats and vulnerabilities are revealed. The manufacturer should also have plans in place to respond to new cyber threats and vulnerabilities (e.g., runbooks, among other things) in a “reasonable timeframe” while the lifecycle of the vehicle is ongoing.
During the post-production stage, which extends to the end of the vehicle’s lifetime, manufacturers must also have the ability to analyze and detect cyber threats, vulnerabilities, and attacks from within vehicle data and logs. Such activities must be in respect to the privacy rights of end-users, in particular concerning consent. Finally, the manufacturer must also demonstrate how cybersecurity dependencies that may exist in its supply chain or among its service providers or subsidiary organizations are managed, also meeting the CSMS requirements listed above.
Requirements for the vehicle – Section 7.3 of the regulation: For the vehicles going through type approval with regards to cybersecurity, approval authorities will begin their compliance audit by verifying that an “exhaustive risk assessment” was performed by the manufacturer and that within this evaluation the vehicle’s critical elements were identified. For each critical element of the vehicle, Approval Authorities will verify that vehicle components and systems were protected with proportionate mitigations to the relevant system or component-risk.
- The vehicle must also be able to perform three central functions to achieve cybersecurity type approval:
Detect and prevent cyber-attacks against. - Support the monitoring capability of the vehicle manufacturer with regards to detecting threats, vulnerabilities, and cyber-attacks.
- Provide data forensic capability to enable an analysis of attempted or successful cyber-attacks.
If cryptographic modules are used in order to comply with this regulation, the manufacturer is required to modules that are in line with consensus standards and if not, satisfactory justification should be provided.
Manufacturers are also required to report at least once a year about their monitoring activities and any detected cyberattacks relevant to the vehicles approved for cybersecurity. Depending on the information reported by the manufacturer, Approval Authorities may require the manufacturer to remedy ineffectiveness in the manufacturer’s reports or response(s) to cyber attacks in the field.
Note
WP.29 UN cybersecurity regulation is an unprecedented vehicle regulation that outlines new processes and technology manufacturers must have within their organizations and vehicles to achieve vehicle type approval with regards to cybersecurity. While created in a similar time frame to other industry-led standards on automotive cybersecurity engineering (e.g., ISO/SAE 21434), WP.29 becomes the first national or international regulation on the topic of cybersecurity for connected and autonomous vehicles. The requirements and text of WP.29 were approved and published in June 2020 on the UNECE / WP.29 website.






